
Vulnerability Scanning
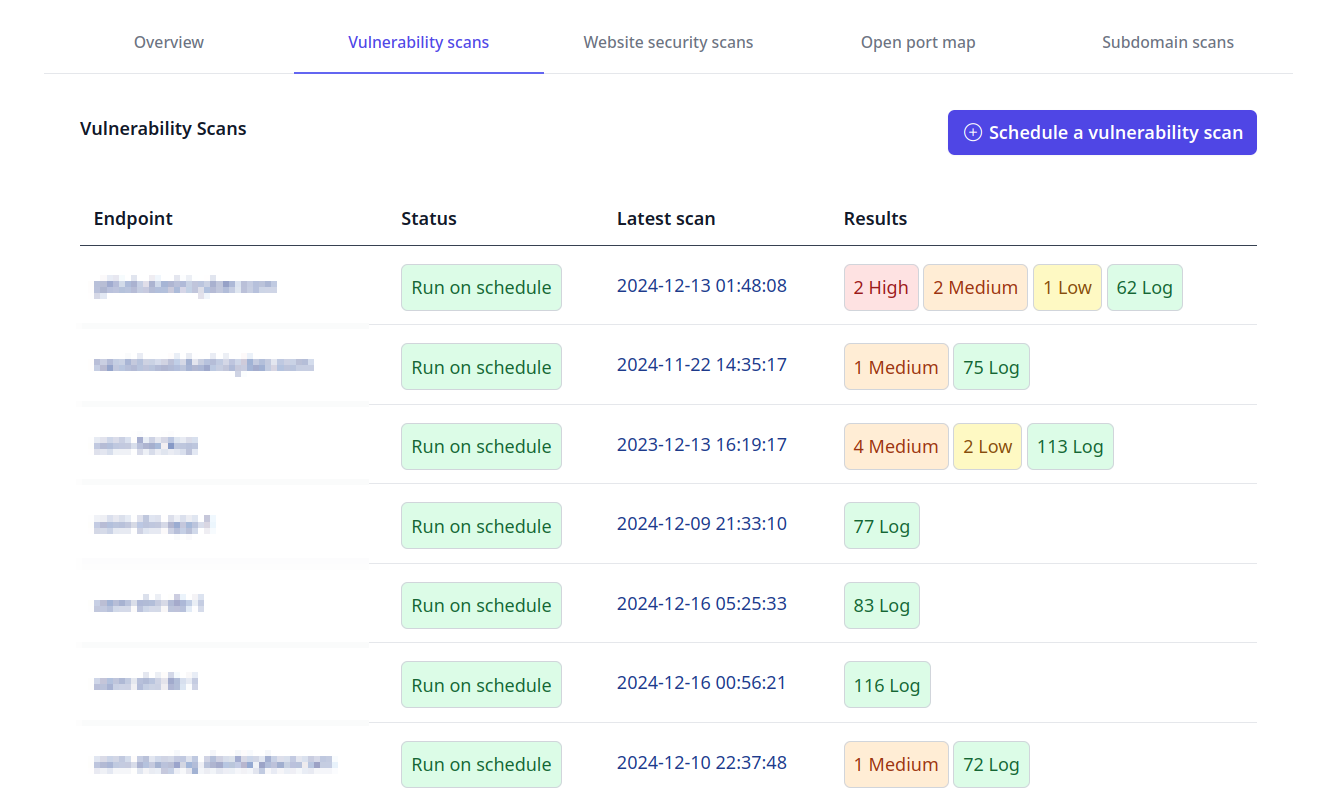
Dashi USM™ vulnerability scanning uses powerful enterprise grade tools to scan your servers for known vulnerabilities. Solution recommendations help you remediate findings before they can be exploited by hackers.
Why is vulnerability scanning important?
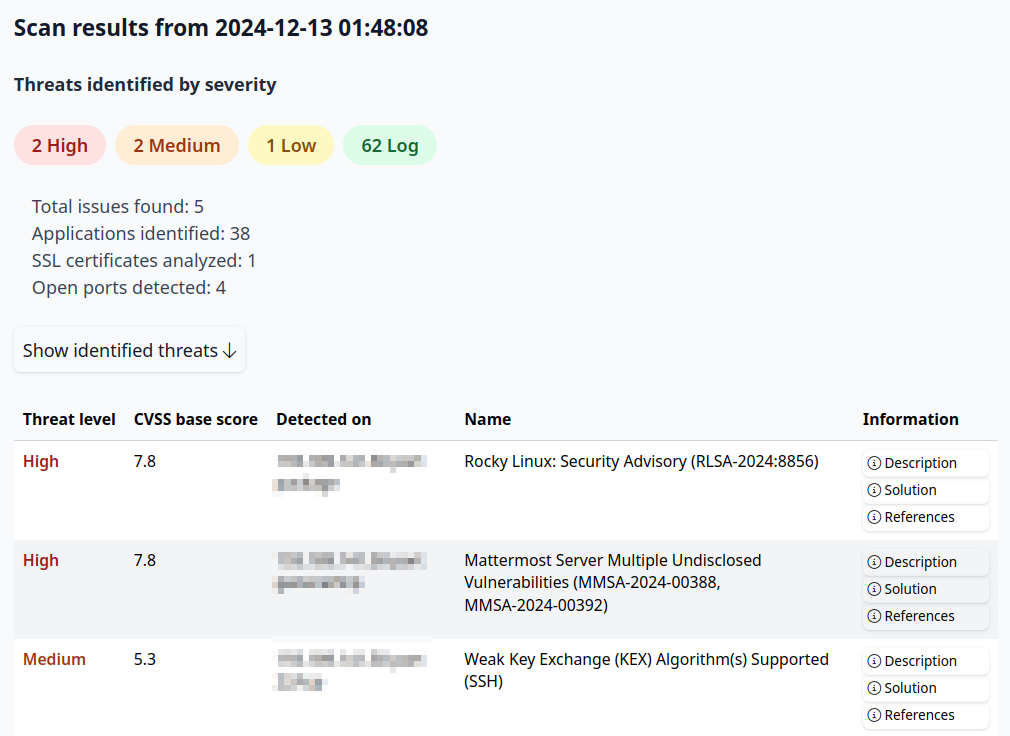
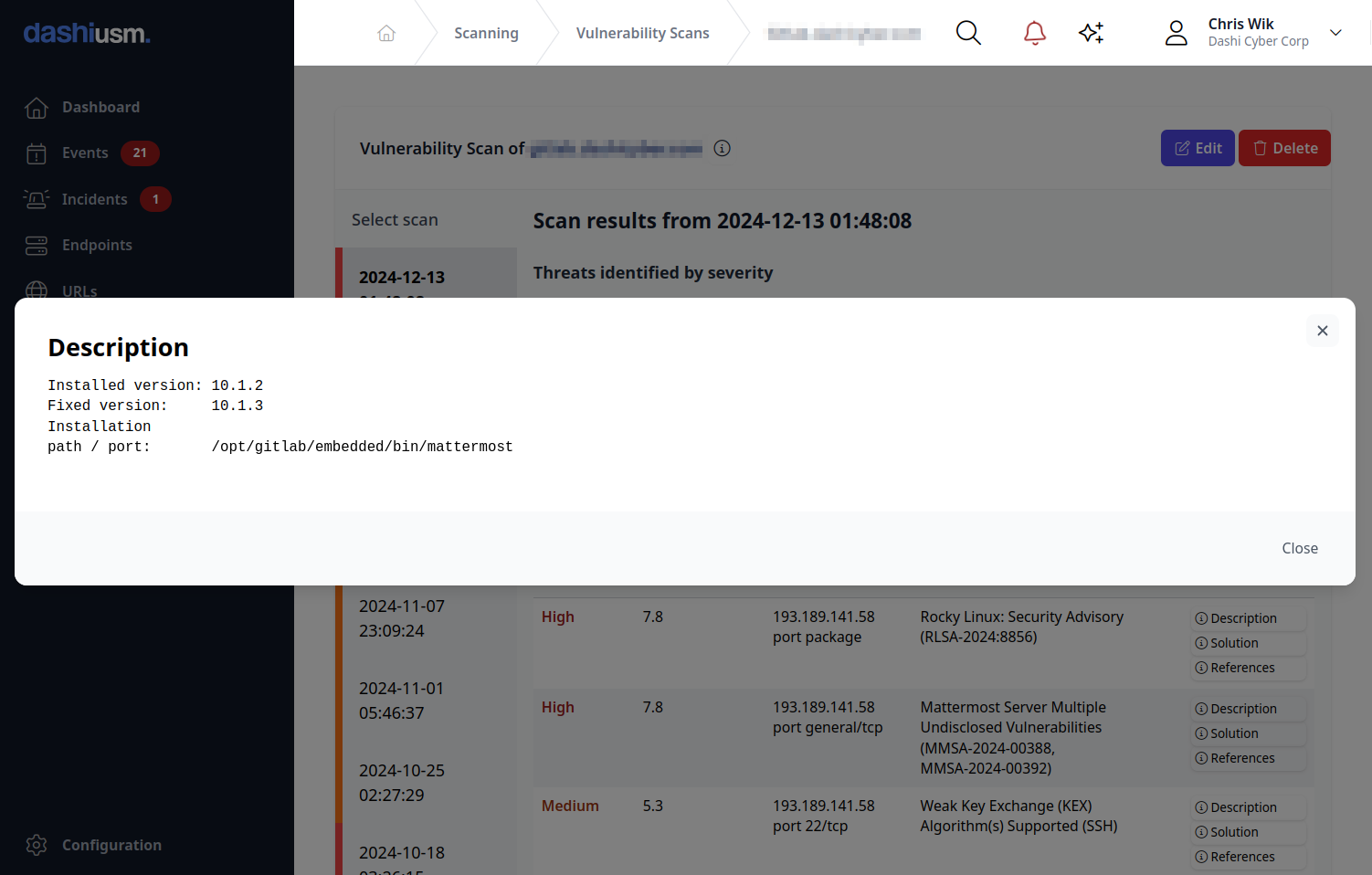
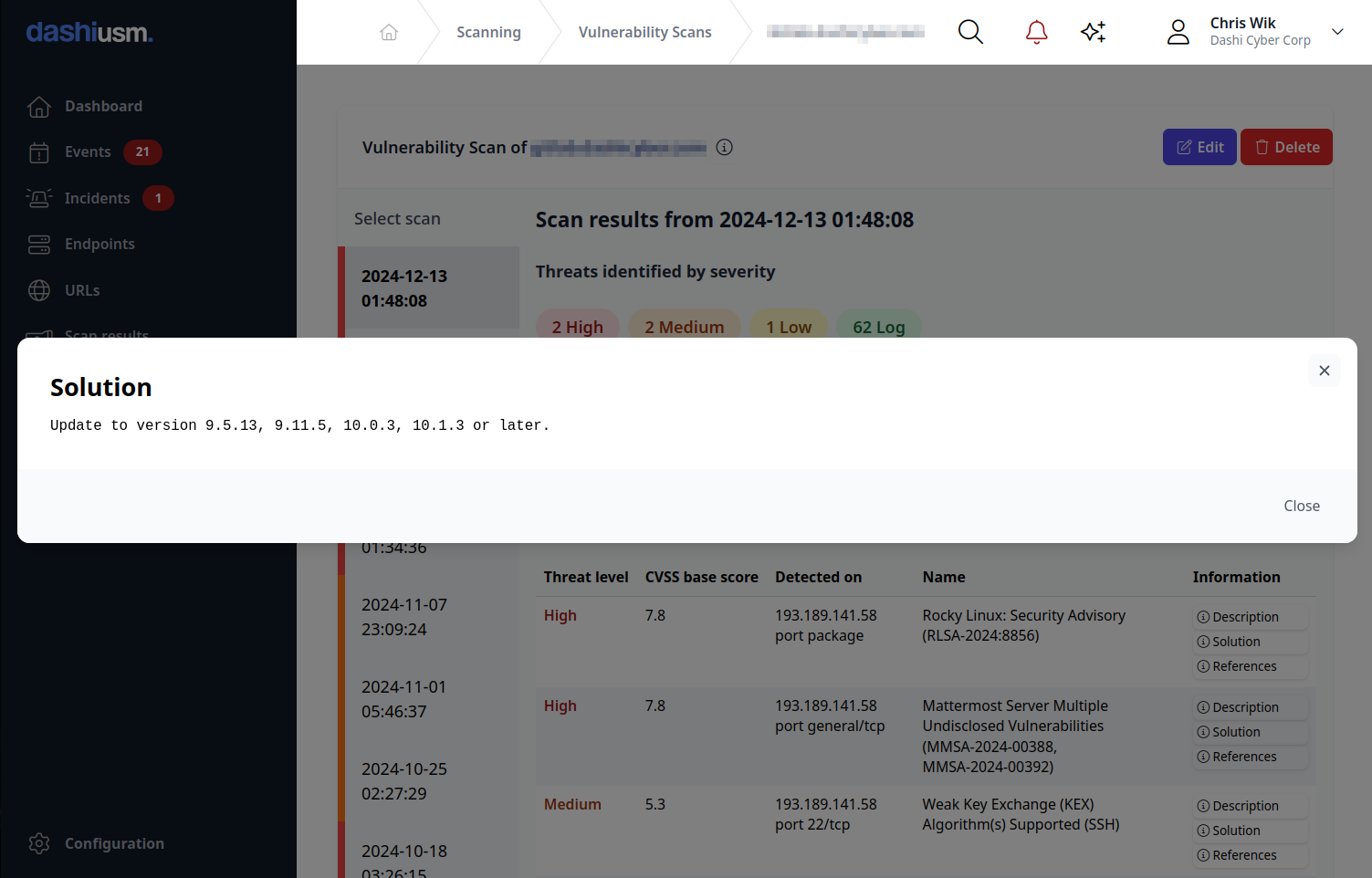
Vulnerability scanning helps you stay one step ahead by proactively scanning your servers for known issues that could be exploitable by hackers. Built-in solution recommendations provide guidance for your system administrators to remediate findings before they can be exploited. Common issues such as weak encryption, insecure configuration, outdated packages and libraries are all identified by vulnerability scanning.
Vulnerability scanning helps you:
- Identify issues. Vulnerability scanning can identify common issues and alert you so you can take proactive steps to remediate them.
- Keep up with changes. The vulnerabilities database our scanners use is constantly being updated. Dashi USM™ notifies you automatically when new vulnerabilities are discovered that affect your servers.
- Remediate findings. Suggested solutions are provided for identified issues, helping your technical team to remediate them quickly and efficiently.
- Demonstrate compliance. Vulnerability scanning is a key part of many compliance standards. Dashi USM™ helps you to demonstrate that you are meeting these requirements.
- Target remediation efforts. See which vulnerabilities have the highest potential for exploitation, and which vulnerabilities have been observed over the longest period of time.
Why use Dashi USM™ for vulnerability scanning?
Three good reasons!
- It's easy. Dashi USM™ doesn't require any special software, and you can get started in minutes.
- It's free. Dashi USM™ offers a free plan that includes 5 vulnerability scanning on a monthly basis.
- It integrates into a broader security framework. Once your results are in you can add comments, tag risks, log corrective actions and more. Dashi USM™ is a complete security management solution.
Vulnerability scanning as a stand-alone activity doesn't give you the full picture. Understanding the risks vulnerabilities present in the context of your organization is key to managing them effectively.
Get started today
Why wait? It's free, including your first 5 vulnerability scans.
Need more scans or more frequent scans? Check out our paid plans.
Behind the scenes
Dashi USM™ uses enterprise grade vulnerability scanning technology based on OpenVAS to remotely scan your servers for known malware, weaknesses, vulnerabilities and misconfigurations.
- No software to install. Dashi USM™ runs the scans for you, so you don't need to install any software on your servers.
- Automatic recurring scans. Never forget to run a scan again. Dashi USM™ runs them for you on the defined schedule, completely automatically. If changes are detected, an Event is generated with details highlighted.
- Authenticated. If remote SSH access is available for your servers, authenticated scans provide significantly more comprehensive results. If your servers are behind a firewall, talk to our technical support team for guidance on how to set up authenticated scans.
- Or unauthenticated. If authenticated scans can't be used or are not required, unauthenticated scans can still provide valuable information. Dashi USM™ can scan your servers from outside your network, just like an attacker would.
Adding structure
Using Dashi USM™ to run your vulnerability scans enables you to feed in the vulnerability report data into your information security management system, turning raw data into actionable intelligence.
- Get structured data. Most people only ever look at the human-readable reports generated by vulnerability scanning tools. Dashi USM™ also stores the structured XML data, enabling a multitude of possibilities for further use and analysis.
- Get a view. Powerful vulnerability reporting tools in Dashi USM™ enable you to analyze scan results and target your remediation efforts for maximum effect.
- Assign impact scores. Identified vulnerabilities are scored based on the Common Vulnerability Scoring System (CVSS). CVSS scores do not however take into account the specific impact based on your unique environment. In many instances, a vulnerability may be rated as high, but the impact to your organization may be low. Dashi USM™ will guide you through the process of assigning impact scores for Confidentiality, Integrity and Availability (the CIA triad) for each Event generated by the vulnerability scanning process, giving you a more accurate view of the risk to your organization.
- Tag risks. When a scan report is arrives into Dashi USM™, an Event is generated and flagged up for review. Tagging relevant risks from your Risks register is quick and easy, and helps you track and prioritize risk treatment for high impact risks.
- Follow-up. If action is required, log a Change or a Corrective Action in Dashi USM™ to track the resolution of the issue.