Port Scanning
Add your endpoints to Dashi USM™ and it will immediately begin scanning for open ports and running services.
Why is port scanning important?
Understanding your attack surface is of critical importance when it comes to securing your data. The port scanning feature in Dashi USM™ helps to identify all the open ports and services running on your public facing servers. This helps build a picture of your attack surface.
Port scanning helps you:
- Know what ports and services are exposed to the public Internet. If ports are open that should only be accessible to system administrators or staff, this could be a security risk.
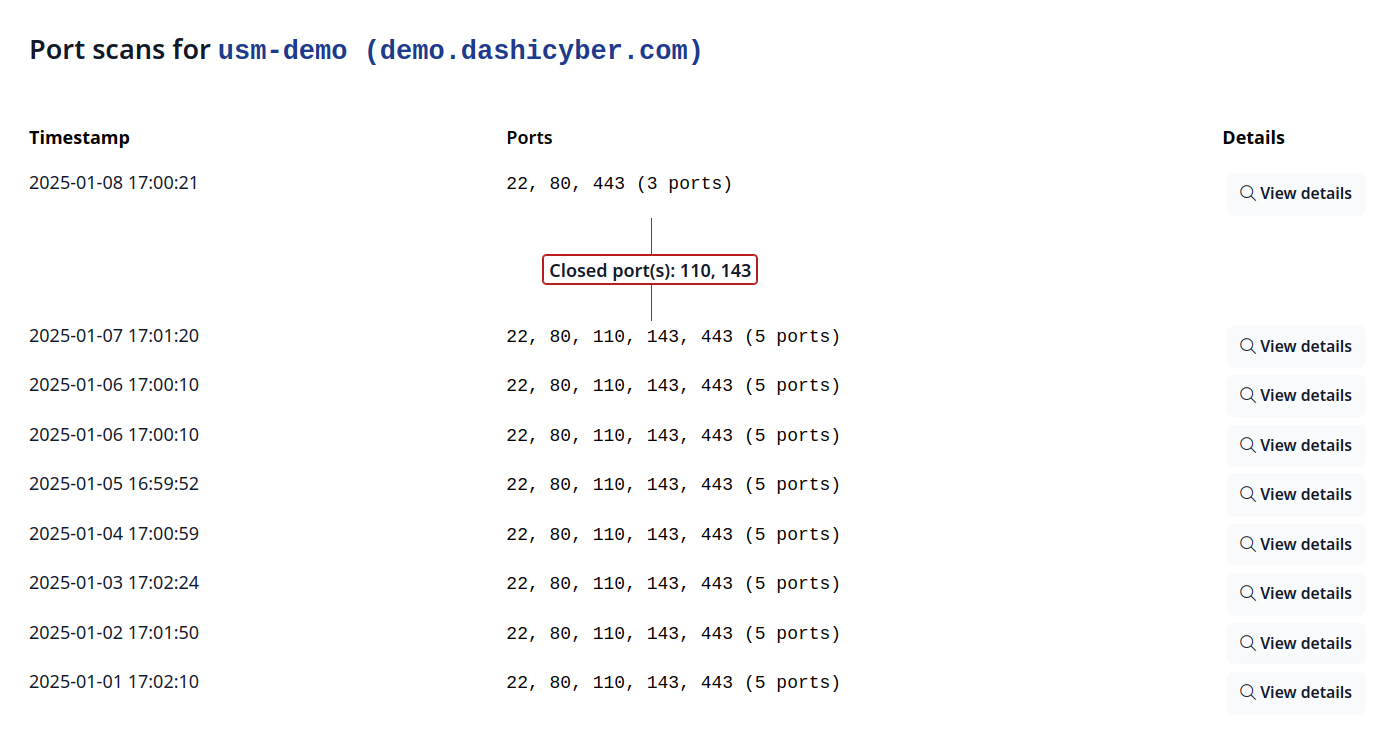
- Know when changes are made. Dashi USM™ automatically rescans all your endpoints daily, and generates Events whenever ports are opened or closed on your endpoints. This can give you a critical heads up if an attacker has made unauthorized changes or installed a backdoor.
- Maintain a paper trail. Every time a port scan detects changes, add a comment to the Event to document the change. If you need to investigate a security incident, you'll have a record of when changes were made any why. Easily search your Events to find the information you need.
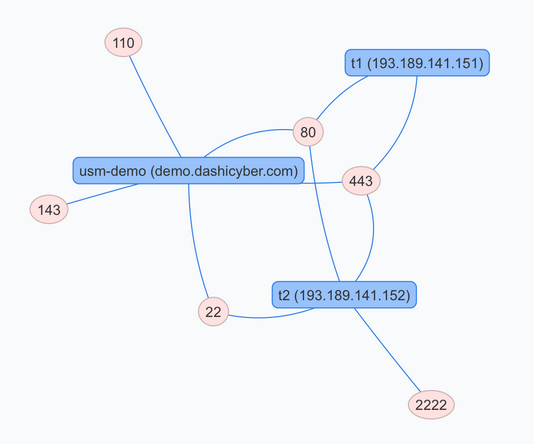
- Get a visual. Dashi USM™ provides a visual port map of your endpoints and the ports that are open on them.
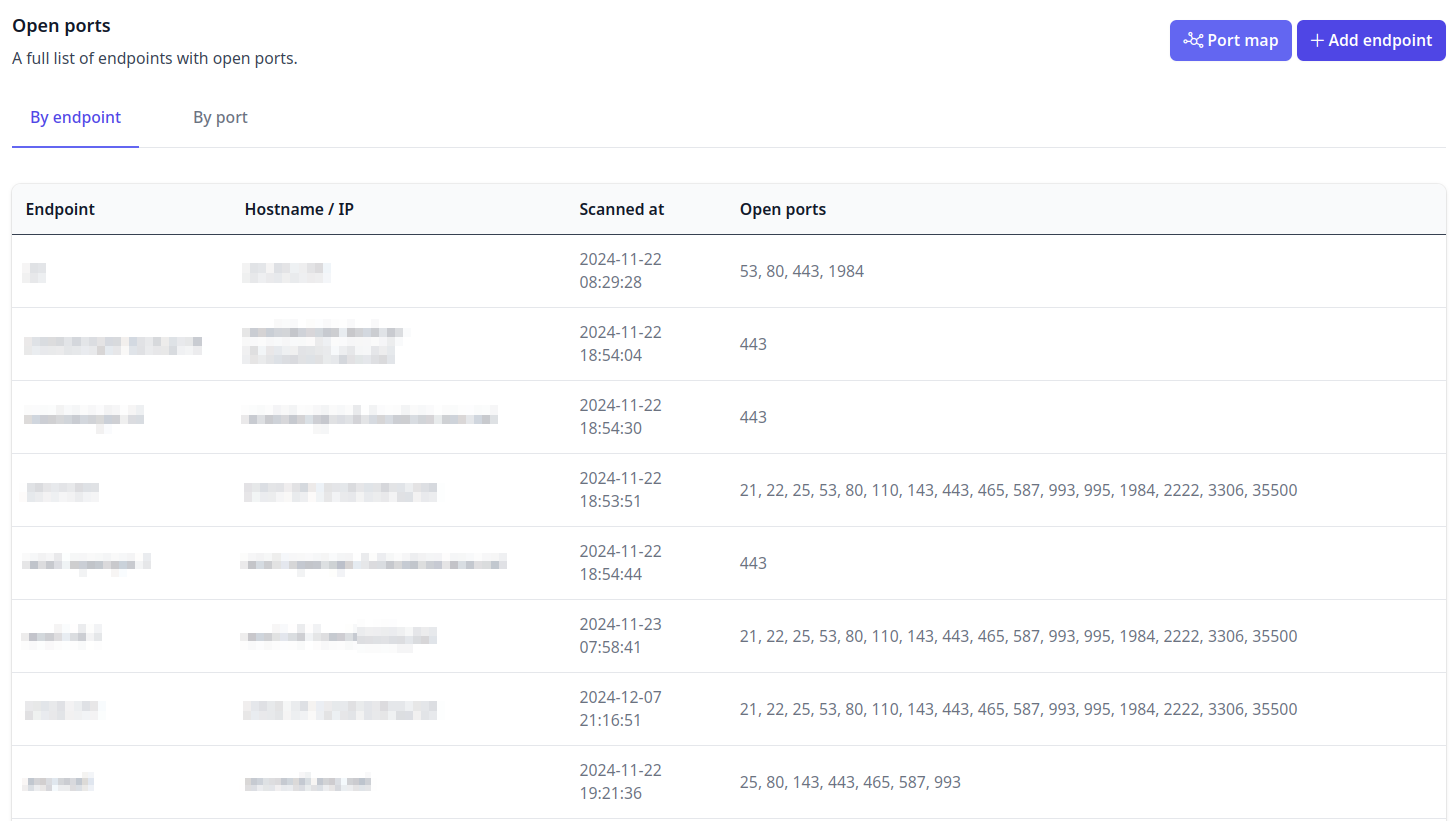
- Audit. See which ports are open by endpoint or by port. Make sure you're only exposing the ports you need to.
Behind the scenes
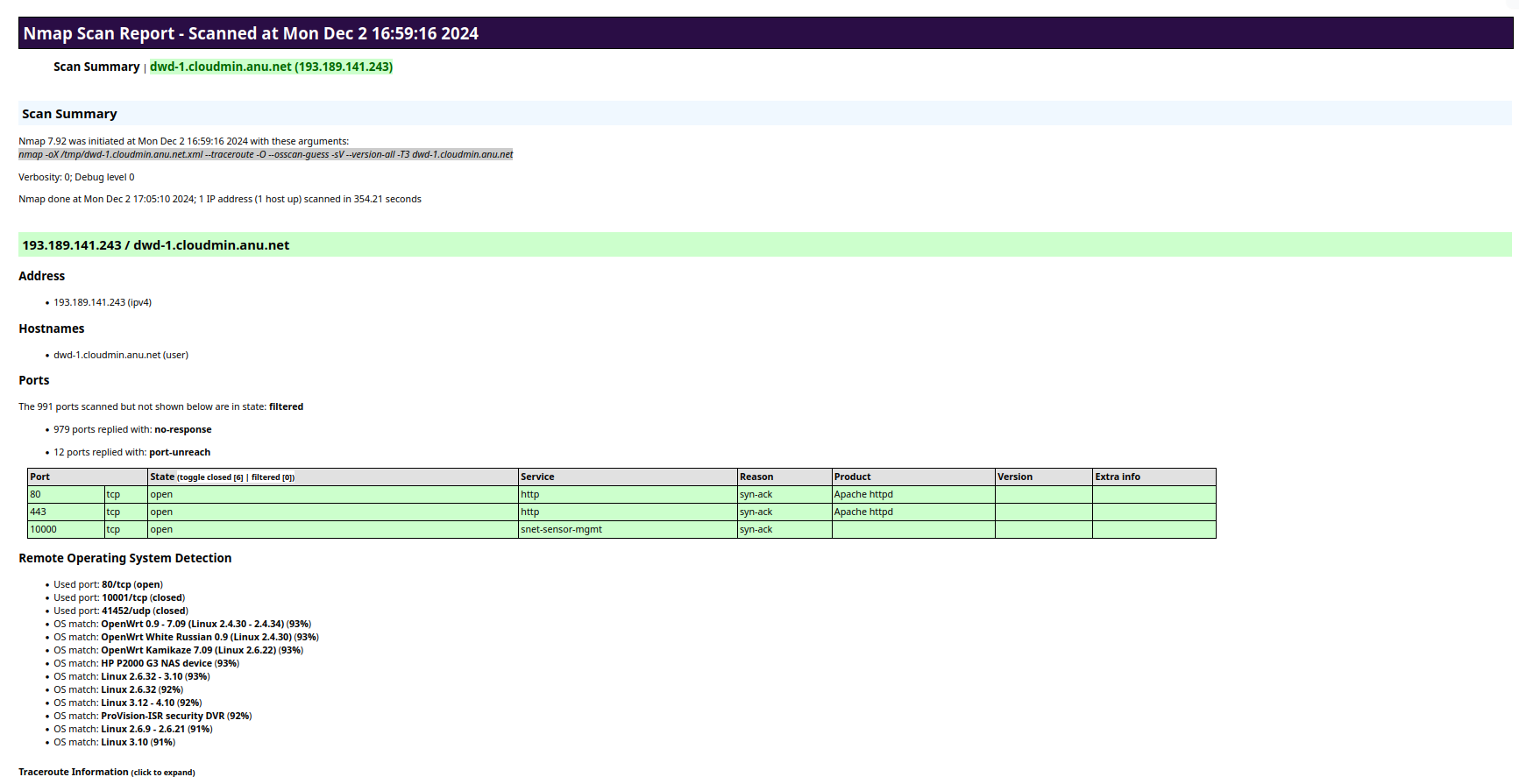
Dashi USM™ uses the open source nmap utility to scan your endpoints for open ports and services. nmap is a powerful open source tool that can be used to scan networks and discover vulnerabilities. So why not just use nmap directly? Dashi USM™ adds functionality by:
- Display the graphical report. No need to figure out the right Terminal command and necessary privileges, or decipher the default text based nmap output. Dashi USM™ displays the results in a graphical format.
- Automatic recurring scans. Never forget to run a scan again. Dashi USM™ runs them for you every day, completely automatically. If changes are detected, an Event is generated with details highlighted.
- Store the results for all your endpoints in one place. Dashi USM™ parses the XML output so you can view open ports and their associated endpoints on a graphical map, or bring up the Open Ports Report to list open ports by Endpoint (which ports are open on each Endpoint) or by Port (which Endpoints have a specific port open).
- Scan from outside your network. Dashi USM™ runs nmap from a server outside your network, so you can see what an attacker would see.
Adding structure
Using Dashi USM™ to run your port scans enables you to feed in port scan data into your information security management system, turning raw data into actionable intelligence.
- Get structured data. Most people only ever look at the human-readable reports generated by port scanning tools. Dashi USM™ also stores the structured XML data, enabling a multitude of possibilities for further use and analysis.
- Get a view. From the Asset Exposure Report, you can see which ports are open on each Endpoint that stores or processes any given information asset. Want to know where your internal documentation might be exposed? Bring it up in the Asset Exposure Report, and you'll see a list of Endpoints that store or process the asset, the ports that are open on each Endpoint, along with any vulnerabilities that have been detected, risks that have been tagged, locations of endpoints pinned on a map, and more.
- Assign impact scores. Dashi USM™ will guide you through the process of assigning impact scores for Confidentiality, Integrity and Availability (the CIA triad) for each Event generated by the port scanning process.
- Tag risks. Ports which are open but should not be can pose a risk to your organization. By tagging risks from your risk register such as "Network attack", "Malware" or "Data breach", you will be able to see the impact of the open ports in your risk register.
- Follow-up. If action is required, log a Change or a Corrective Action in Dashi USM™ to track the resolution of the issue.
