
Risk Management
Risk management may sound boring, but it doesn't need to be hard or time-consuming, and it's incredibly important. Risk management is the process of documenting which risks your organization is faced with, the potential consequences should they be realized, and the options available to reduce or eliminate them. Then, you can make informed decisions about which risks to treat, and how, and track your progress.
How it works
Dashi USM™ is a powerful tool for managing information security risks. Here's how it works.
-
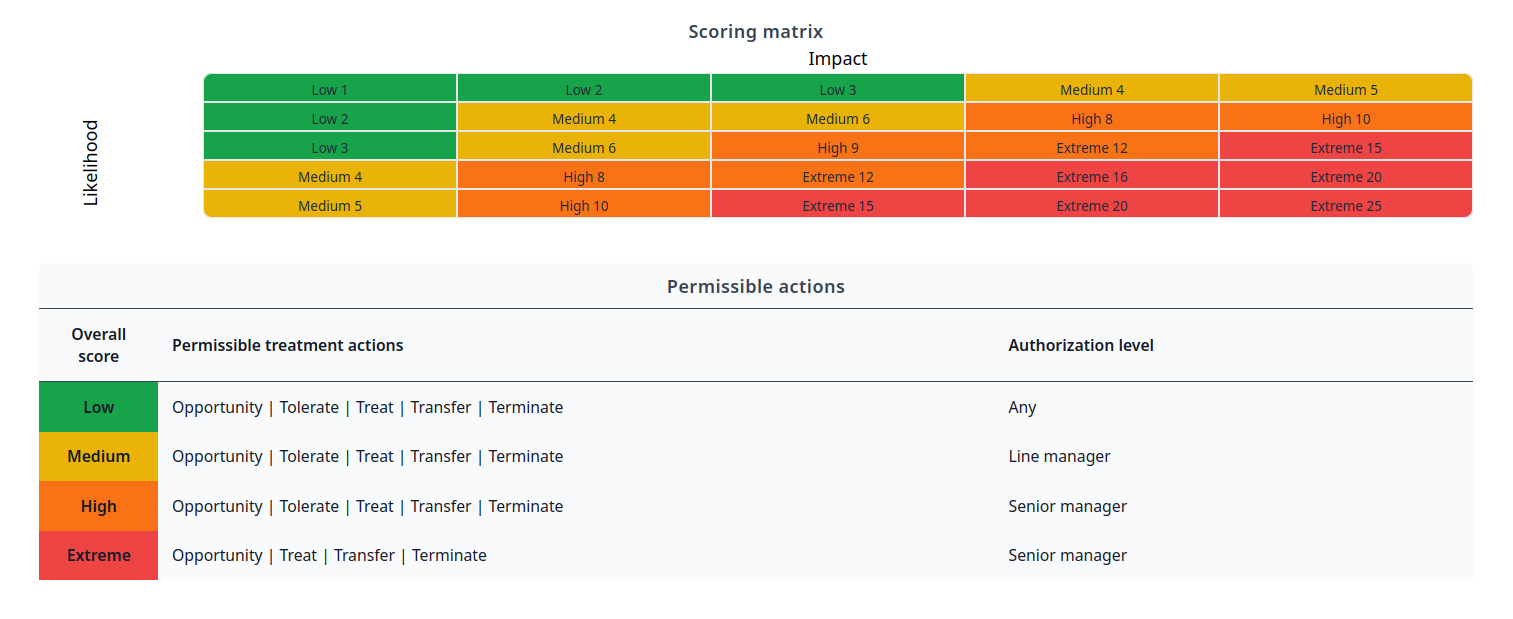
Define your criteria.
Configure your risk criteria to match your organization's risk appetite in the Dashi USM™ settings.
Identify the permissible actions for each level of risk.
-
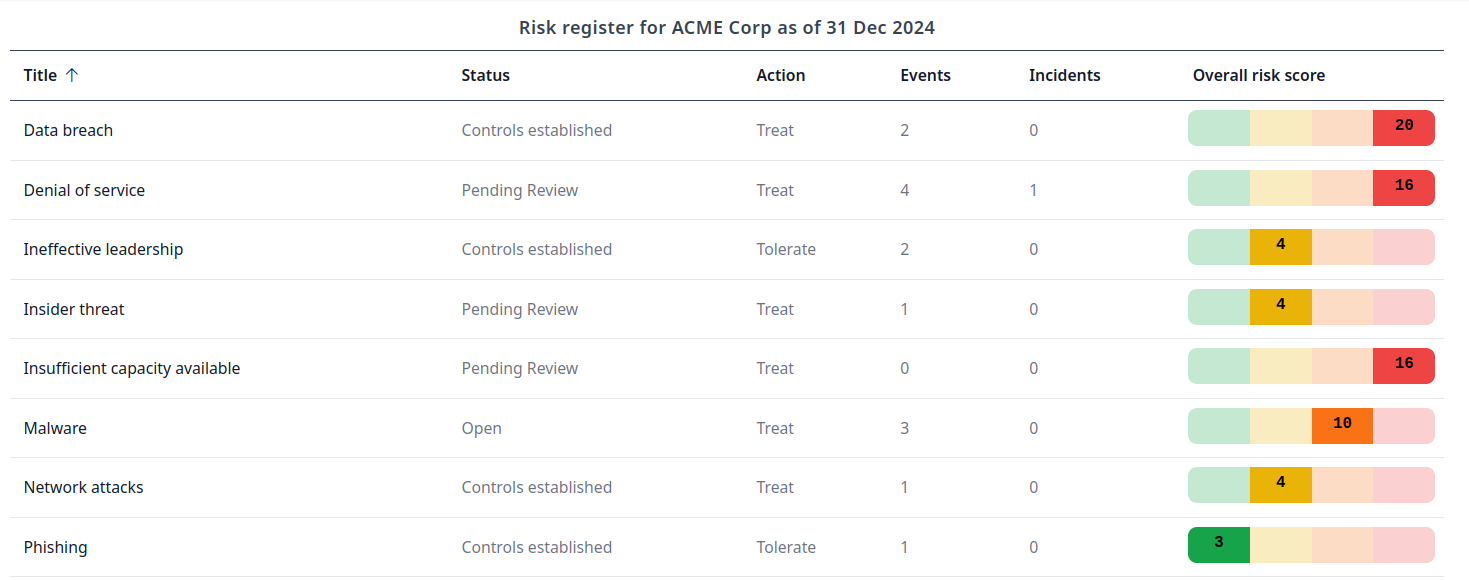
Create your risk register.
Add risks to your Risk Register in Dashi USM™. A pre-built Risk Register is included to get you started.
-
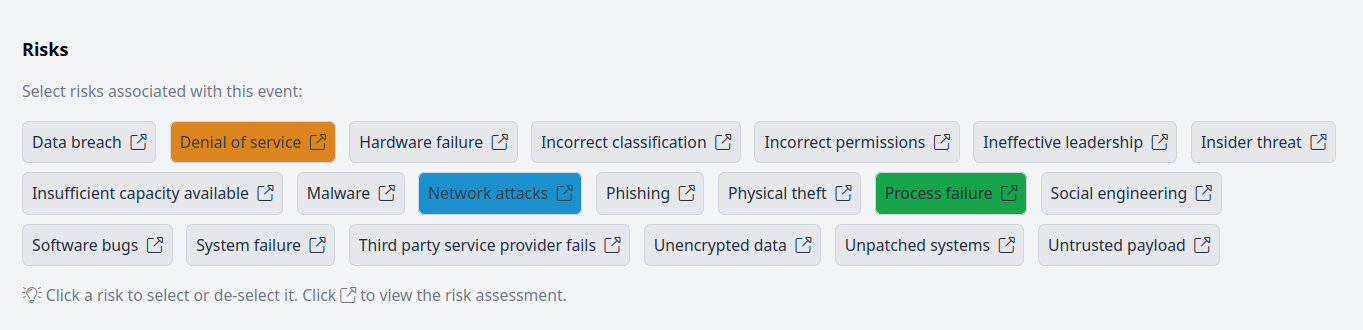
Tag risks when things happen.
When an Event occurs, tag the risks that are associated with it. This helps you to track and prioritize risk treatment.
-
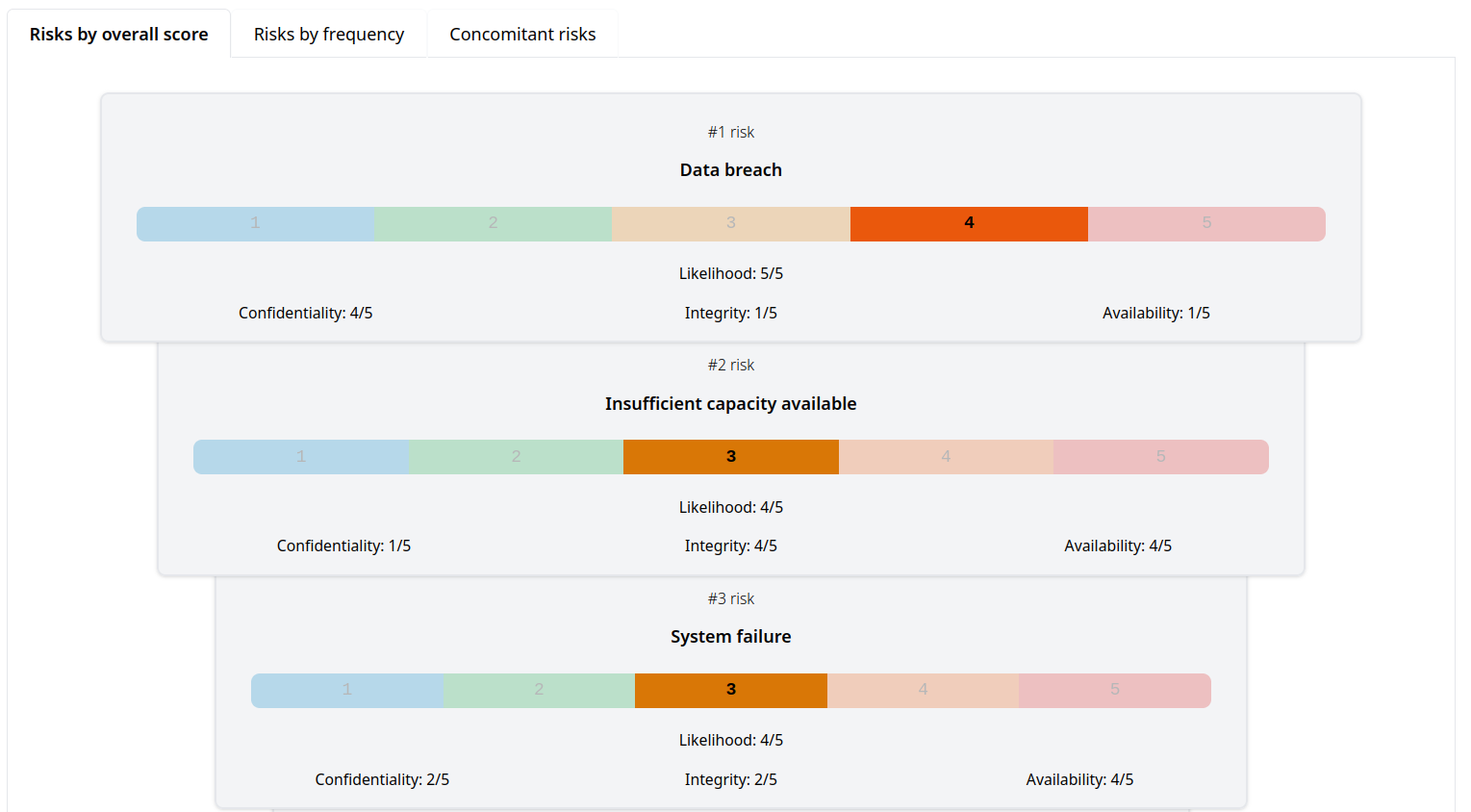
Analyze and prioritize.
Use the Risks Report and risk detail views to understand the assessed and actual risks to your organization.
Plan and prioritize risk treatment based on the impact and likelihood of each risk.
Fully integrated
In Dashi USM™, risk management is fully integrated into your Information Security Management System.
- Tag risks: events. In the Event detail view you can tag risks from your Risks register, helping you to track and prioritize risk treatment for high impact risks.
- Tag risks: incidents. If an incident resulted in a risk being realized, tag the risk in the Incident detail view. This helps you to track and prioritize risk treatment for high impact risks, or risks that are repeatedly realized.
- Link to Controls. Easily cross-reference Risks with applicable Controls so you can see at a glance which Controls are in place to mitigate each Risk.
- Drill-down from Endpoints. From the endpoint detail view, you can see which risks are associated with the endpoint, based on the assets it stores or processes. This helps you to understand the potential impact of a security incident on the endpoint, and make sure it is protected appropriately.
- Drill-down from Assets. Use the Asset Exposure Report to get a high level view of the potential exposure of each information asset including the attack surface, detected vulnerabilities, and selected risks. See which controls are in place to mitigate the risks.
- Drill-down from Policies. Policies reference Controls, and Controls reference Risks. So you can easily drill down from a Policy to the Risks that it is designed to mitigate.
- Follow-up. If action is required to remediate a risk, log a Corrective Action in Dashi USM™ to track the resolution of the issue. From the risk detail view, you can see which corrective actions have been documented, and their current status.
Why use Dashi USM™ for managing information security risk?
Three good reasons!
- Get a kick-start with a pre-built Risk Register Dashi USM™ comes with a pre-built Risk Register that gives you a great starting point to think about the risks to your organization. Adding, editing and deleting risks is easy and intuitive.
- It's easy. Dashi USM™ is Web based and easy to use. No special software or training required.
- It's free. The risk management module is included free on all our plans, including free.
Get started today
Why wait? It's free, including 5 vulnerability scans and 30 days of event data retention.
Need more? Check out our affordable paid plans.