
ISO 27001 Information Security Management System
Dashi USM™ is a complete Information Security Management System based on the ISO 27001 standard.
Building an ISMS can seem like a daunting task, especially if you have limited experience, tight budgets or a small team. Our goal with Dashi USM™ is to make it as easy as possible for you to build a professional, audit-ready ISMS for your organization, quickly, and completely free.
What is an Information Security Management System
ISO 27001 is an international standard for Information Security Management Systems (ISMS). It provides a systematic approach to managing sensitive company information so that it remains secure. It protects your people, processes and IT systems by applying a risk management process.
The standard is designed to ensure the selection of adequate and proportionate security controls that protect information assets and give confidence to interested parties, such as customers or regulators.
The components of the Management System in Dashi USM include:
-
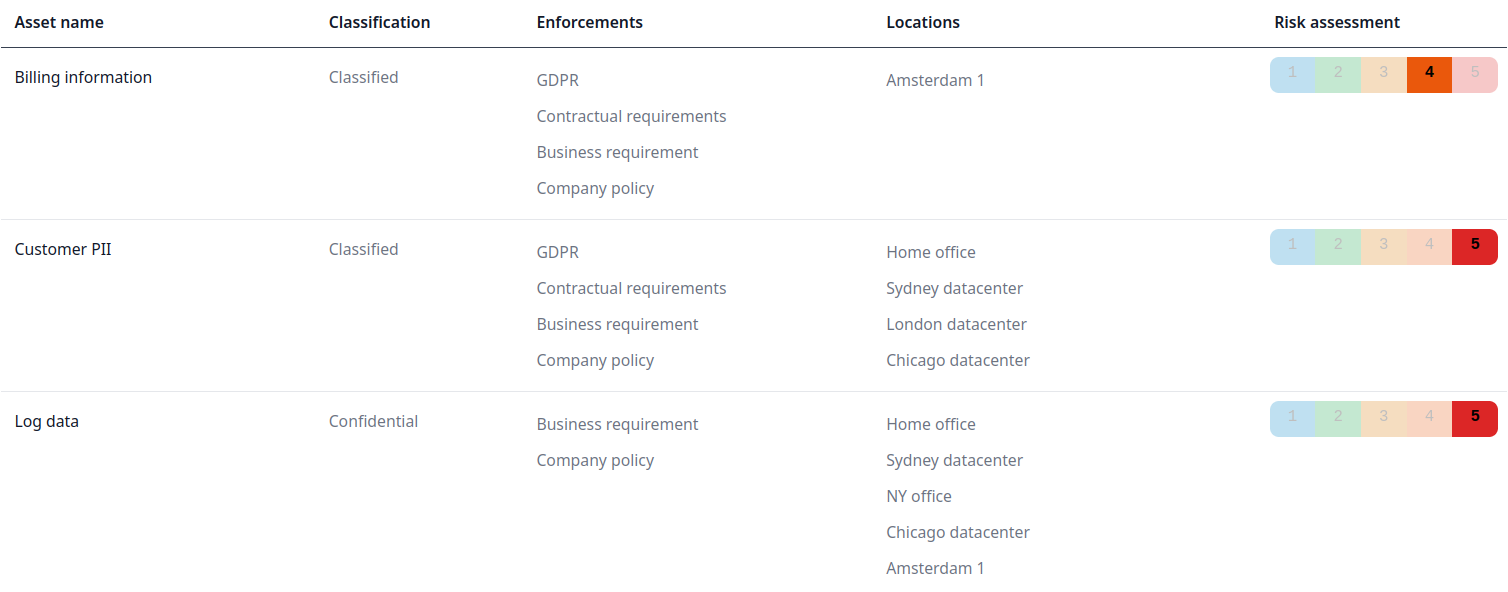
Asset inventory.
Keep track of your information assets, where they are stored and processed, and the risks and vulnerabilities they are exposed to.
-
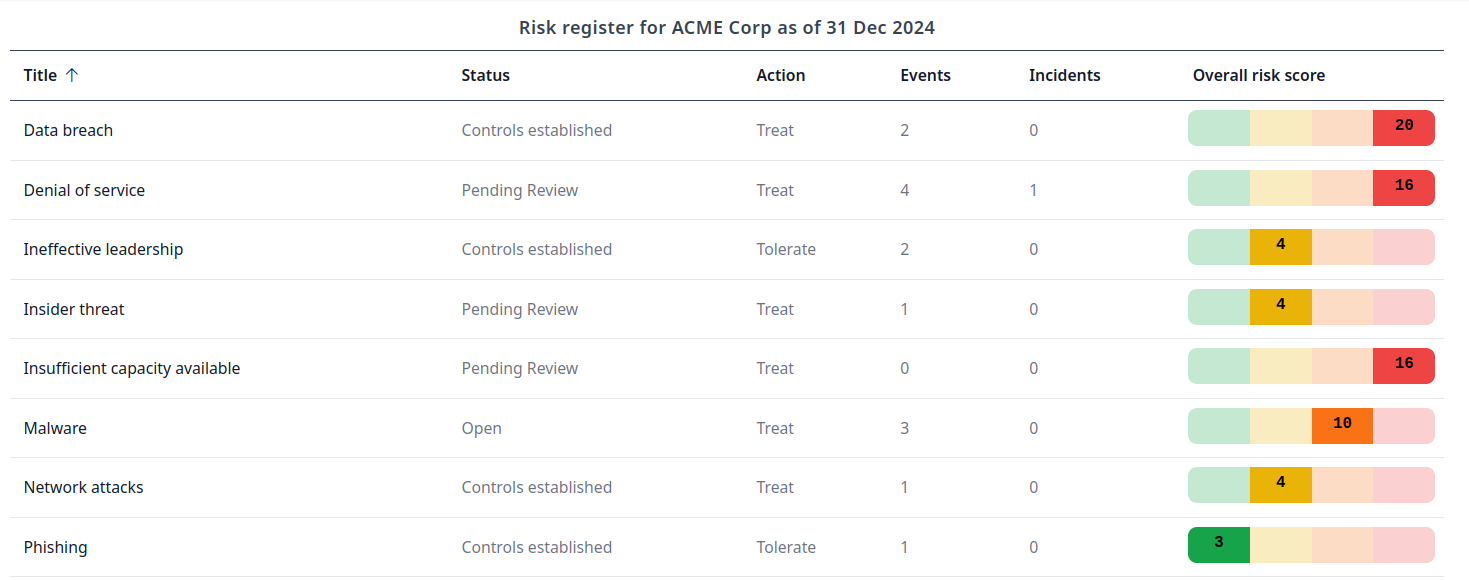
Risk register.
Keep track of risks your organization is exposed to in the Risk Register. A pre-populated Risk Register is included to get you started.
-
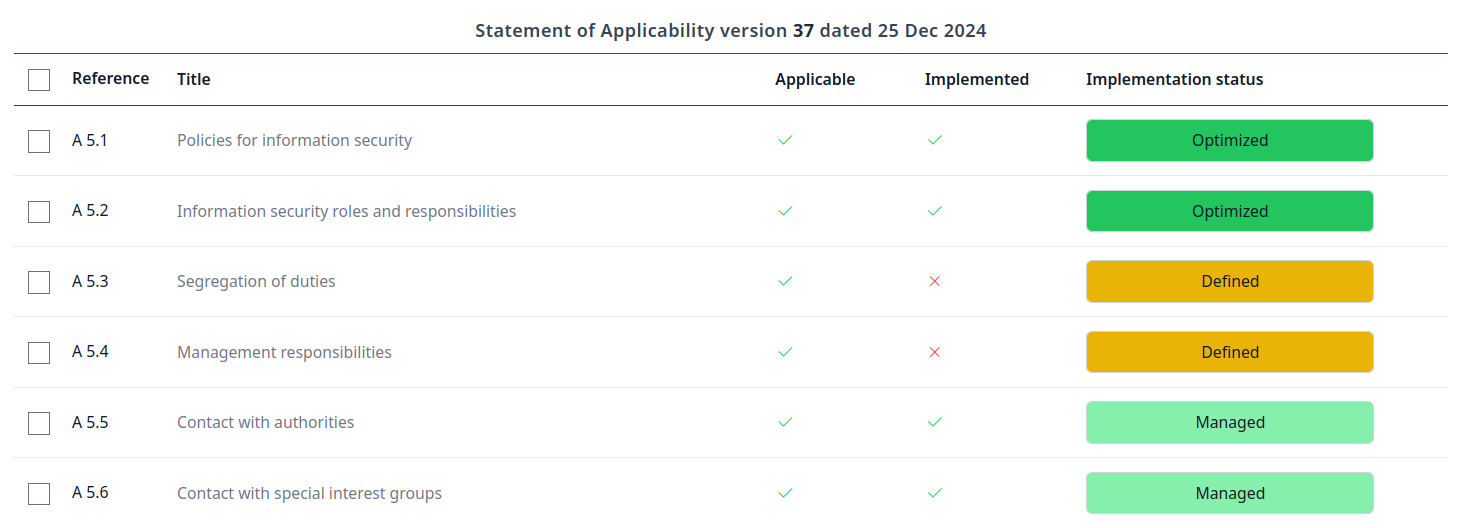
Controls (Statement of Applicability).
Define and document the controls that are in place to mitigate the risks in your organization.
In ISO 27001 terminology, this is called the Statement of Applicability.
-
Policies.
Define and document the policies that are in place to protect information in your organization.
Cross-reference your controls with the policies that they are designed to enforce.
Policies are automatically version controlled.
Track user policy acceptance.

-
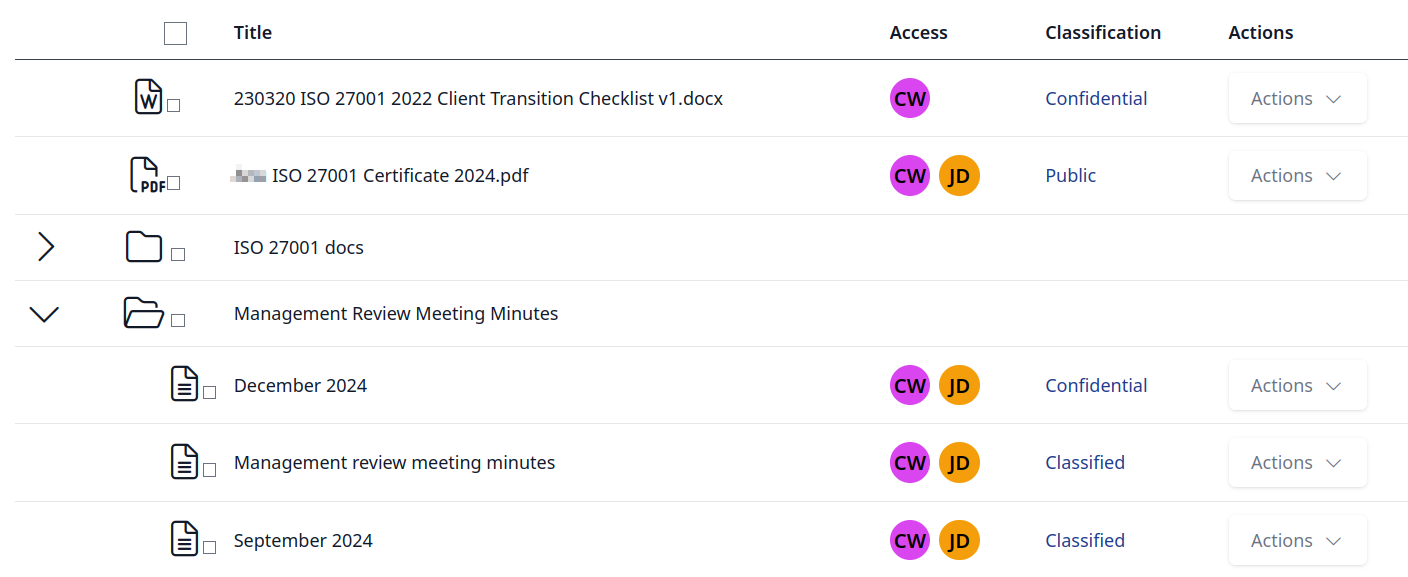
Documents.
Create and share version controlled rich text documents with your team using the built-in editor.
Upload PDFs, office docs or other related documents that form part of your ISMS.
Organize documents into folders, and tag them with classifications.
-
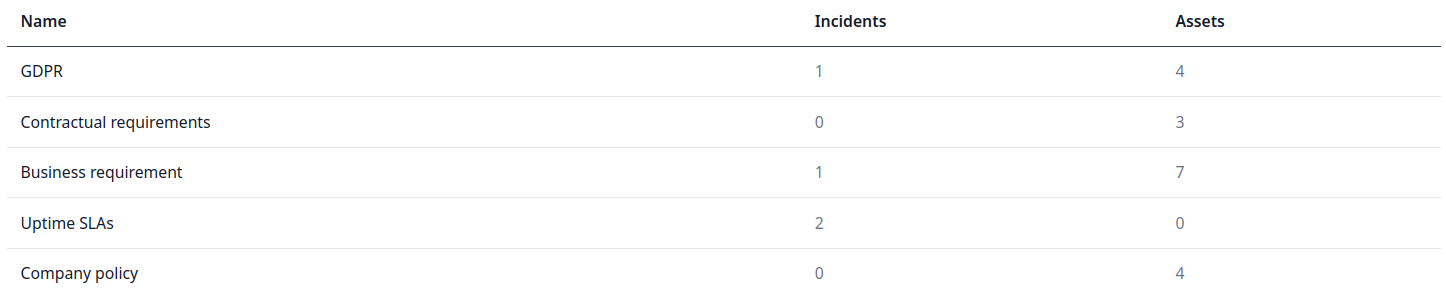
Enforcements.
Define and document the enforcements. These are the mechanisms by which your organization is compelled to protect information.
For example: legal or regulatory requirements, contractual requirements, service level agreements, and internal business requirements.
-
Classifications.
List and describe the classifications in use to label and protect information in your organization.
-
Corrective Actions Log.
Log corrective actions that are required to remediate risks in your organization.
Why use Dashi USM™ for your ISMS?
Three good reasons!
- Get a kick-start with a pre-populated data Dashi USM™ helps you to get started quickly with a pre-built Risk Register, ISO 27001 Controls list, starter Policies, Classifications and more.
- It's more than just an ISMS. Dashi USM™ integrates endpoint management, security scanning tools, event management, incident logging and corrective actions directly into the ISMS. This transforms your ISMS from a paperwork exercise to a functional system that actually helps you secure your systems.
- It's free. Dashi USM™ is free to use, including 5 vulnerability scans and 30 days of event data retention. The entire ISMS functionality is free of charge on all plans.
Get started today
Why wait? It's free, including 5 vulnerability scans and 30 days of event data retention.
Need more? Check out our affordable paid plans.
More than just an ISMS
Say goodbye to maintaining disparate systems, manual cross-referencing and endless Word and Excel documents. Dashi USM™ integrates endpoint management, security scanning tools, event management, incident logging and corrective actions directly into the ISMS. Everything you need to manage information security risk in one place.
- Vulnerability scans. Run vulnerability scans on your servers to identify weaknesses that could be exploited by attackers. Results feed directly into the Events feed in Dashi USM™, from where you can track and prioritize remediation.
- Website and API scans. Run security scans on your websites and APIs to identify weaknesses that could be exploited by attackers. Results feed directly into the Events feed in Dashi USM™, from where you can track and prioritize remediation.
- Attack surface mapping. Built-in Endpoint management helps you to keep track of your servers, workstations, and other devices. Subdomain discovery helps you to identify all the subdomains associated with your organization. Port scans help you to identify open ports and services that could be exploited by attackers. Asset Exposure Report, Open Ports Report, and interactive port map tools help you to understand your attack surface.
- Event management. Comprehensive Event Management helps you to track security events in your organization. Events are automatically generated from vulnerability scans, security scans, and other sources. Tag risks, add comments, view repeat events, follow up with corrective actions or escalate an Event to an Incident.
- Incident management. When an Event results in a violation of one or more of your defined enforcements, escalate it to an Incident. Build a timeline, flesh out the details of what happened, follow up with corrective actions, log root cause analysis, and track the incident resolution.
- Everything is automatically cross-referenced. No more digging through spreadsheets. Dashi USM™ automatically cross-references your events with your assets, risks, controls, policies, enforcements, classifications, incidents, and corrective actions. Easily follow the trail from an Event to the Risk it is associated with, the Control that is designed to mitigate the risk, and the Policy that enforces the control.